Cyber attacks: increasingly prevalent in today's interconnected world, threaten individuals and organizations. These attacks can compromise data, disrupt operations, and damage reputations. Understanding the risks and implementing effective countermeasures is crucial.

7 Important Steps to Cyber Crime Prevention for Businesses - Source blog.megaventory.com
Editor's Note: Understanding Cyber Attack: Threats, Prevention, And Mitigation Strategies is critical for safeguarding your assets, ensuring business continuity, and preserving trust.
Through rigorous analysis and extensive research, we crafted this comprehensive guide to empower you with the knowledge and strategies to combat cyber threats effectively.
Key Differences and Takeaways
The table below highlights the key distinctions and insights from this guide:
| Element | Key Takeaways |
|---|---|
| Threats | Identification and understanding of various cyber attack methods and their potential impact. |
| Prevention | Implementation of proactive measures to shield systems and data from unauthorized access or attacks. |
| Mitigation | Strategies to respond to and recover from cyber attacks, minimizing damage and restoring normal operations. |
Transition to Main Article Topics
FAQ - Cyber Attack: Threats, Prevention, And Mitigation Strategies

Cyber security threat detection and mitigation using IT discovery | Virima - Source virima.com
Question 1: What are the most common types of cyber attacks?
Cyber attacks can take many forms, including:
- Malware: This is a broad term that encompasses any type of malicious software, such as viruses, worms, or trojan horses.
- Phishing: This is a type of social engineering attack that tricks victims into giving up their personal information or login credentials.
- DDoS attack: This type of attack overwhelms a website or server with traffic, making it inaccessible to legitimate users.
- Man-in-the-middle attack: This type of attack allows an attacker to intercept communications between two parties, such as a user and a website.
Question 2: What are the best ways to prevent cyber attacks?
There are a number of steps you can take to prevent cyber attacks, including:
- Use strong passwords and change them regularly.
- Keep your software up to date.
- Be careful about what you click on or download from email or the internet.
- Use a firewall and antivirus software.
- Back up your data regularly.
Question 3: What should you do if you are the victim of a cyber attack?
If you are the victim of a cyber attack, there are a few things you should do:
- Change your passwords and security questions immediately.
- Contact your bank or credit card company to report any suspicious activity.
- File a police report.
- Contact a cybersecurity expert for help.
Question 4: What are some of the common misconceptions about cyber attacks?
There are a number of common misconceptions about cyber attacks, including:
- Cyber attacks only happen to large corporations.
- Cyber attacks are always easy to spot.
- Cyber attacks are always financially motivated.
- Cyber attacks are always the result of external threats.
Question 5: What are the emerging threats in cyber security and how can we prepare for them?
There are a number of emerging threats in cyber security, including:
- Artificial intelligence (AI) and machine learning (ML) will likely be increasingly used in cyber attacks.
- The Internet of Things (IoT) will create new opportunities for attackers to target devices.
- Cloud computing will continue to be a target for attackers.
To prepare for these emerging threats, we can take the following steps:
- Invest in cyber security awareness and training.
- Update our security infrastructure and tools.
- Collaborate with other organizations and law enforcement to share information and best practices.
Question 6: What are the challenges in cyber security and what can be done to overcome them?
There are a number of challenges in cyber security, including:
- The evolving nature of cyber threats: Cyber criminals constantly adapt and develop new attack techniques, making it difficult to stay ahead.
- The lack of qualified cyber security professionals: There is a shortage of qualified cyber security professionals, making it difficult for organizations to protect themselves from cyber attacks.
- The global nature of cyber threats: Cyber attacks can originate from anywhere in the world, making it difficult to track down and prosecute attackers.
To overcome these challenges, we can take the following steps:
- Invest in research and development to develop new cyber security technologies and tools.
- Educate and train the next generation of cyber security professionals.
- Strengthen international cooperation to combat cyber crime.
By taking these steps, we can help to protect ourselves from the growing threat of cyber attacks.
Tips
Here are some recommended tips to help protect your business from the threat of a Cyber attack: Threats, prevention, and Mitigation strategies.
Tip 1: Regularly update software and systems
Keeping software and systems up to date is one of the most important and effective ways to protect against cyber attacks. Software updates often include security patches that fix vulnerabilities that could otherwise be exploited by attackers.
Tip 2: Use strong passwords and multi-factor authentication
Strong passwords are at least 12 characters long and include a combination of upper and lower case letters, numbers, and symbols. Multi-factor authentication adds an extra layer of security by requiring you to provide two or more forms of identification, such as a password and a security code sent to your phone.
Tip 3: Be cautious about clicking on links in emails or text messages
Phishing attacks are common methods used by attackers to trick people into giving up their personal information or clicking on malicious links. Be wary of any links you receive in emails or text messages, especially if they come from unknown senders.
Tip 4: Use a firewall and antivirus software
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Antivirus software protects against viruses, malware, and other threats by scanning files for malicious code.
Tip 5: Back up your data regularly
In the event of a cyber attack, having a backup of your data can be critical. Back up your data to a secure location, such as an external hard drive or a cloud-based backup service.
Tip 6: Educate employees about cybersecurity
Employees are often the weakest link in the security chain. Educating employees about cybersecurity best practices can help them to identify and avoid threats.
By following these tips, you can help to protect your business from the threat of a cyber attack. However, it is important to remember that no single measure is foolproof. A comprehensive cybersecurity strategy that includes a combination of technical and procedural controls is essential for protecting your business from this ever-evolving threat.
For more information on cyber attack prevention and mitigation strategies, please refer to the Cyber Attack: Threats, Prevention, And Mitigation Strategies article.
Cyber Attack: Threats, Prevention, And Mitigation Strategies
Cyber attacks have become an inevitable threat in the digital age, necessitating comprehensive strategies for their prevention and mitigation.
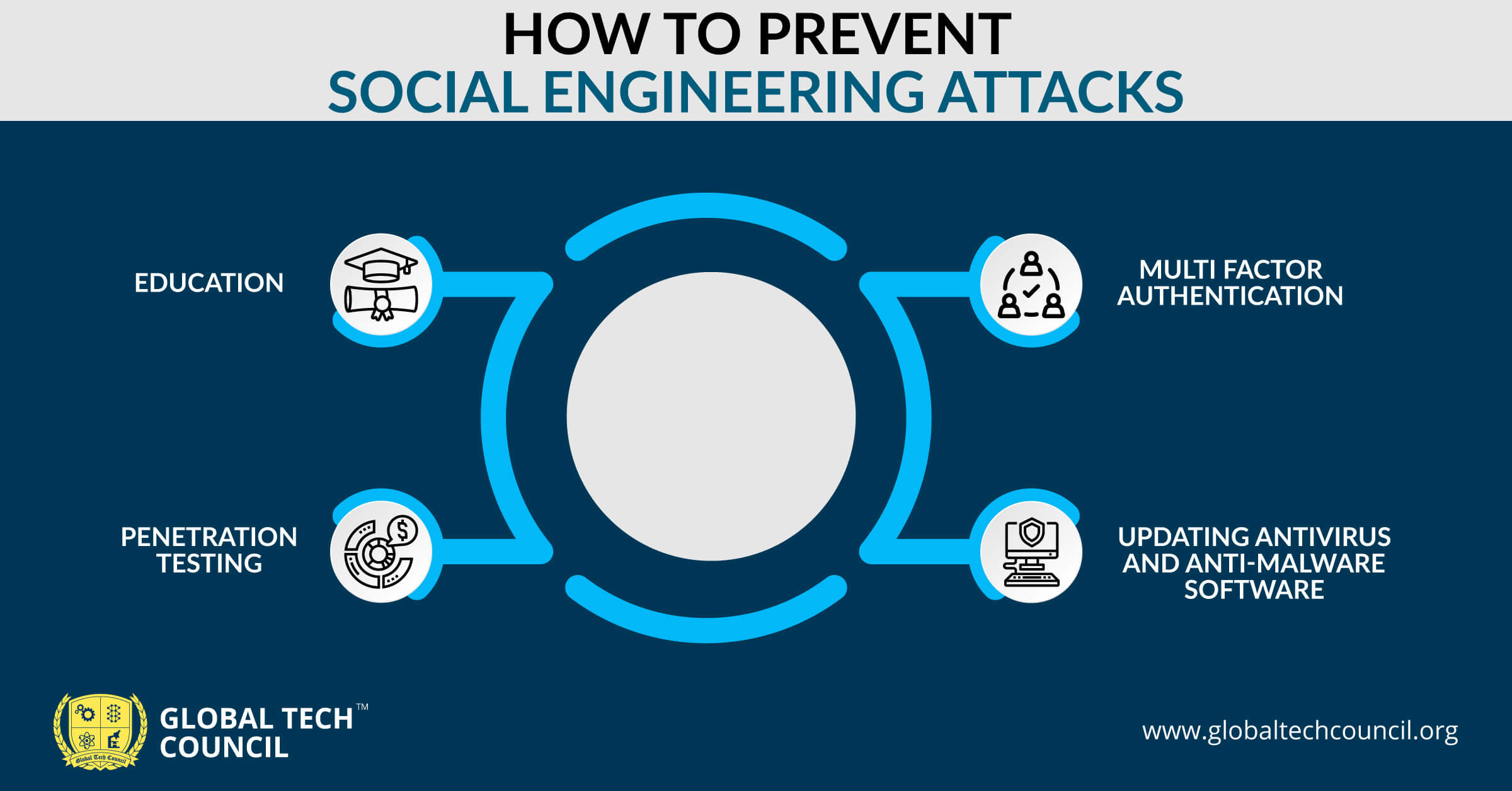
Social Engineering Attacks - What They Are and Some Prevention Tips - Source www.globaltechcouncil.org
These key aspects work synergistically to enhance cybersecurity posture. For instance, threat identification informs network monitoring, which in turn triggers incident response. Security awareness empowers employees to prevent attacks, while software updates and data encryption mitigate their impact. Understanding these aspects empowers organizations to proactively address cyber threats and safeguard their digital assets.
Cyber Attack: Threats, Prevention, And Mitigation Strategies
Cyber attacks are a significant threat to businesses and organizations of all sizes. They can cause financial damage, disrupt operations, and damage reputation. In order to protect themselves, organizations need to understand the different types of cyber attacks, the threats they pose, and the prevention and mitigation strategies that can be implemented. This article provides an overview of cyber attacks, including the different types, the threats they pose, and the prevention and mitigation strategies that can be implemented.

10 Ways to Prevent a Cyber Attack | KBI - Source kbigroup.com.au
There are many different types of cyber attacks, each with its own unique threats. Some of the most common types of cyber attacks include:
- Malware: Malware is a type of software that is designed to damage or disable a computer system. Malware can be spread through email attachments, downloads, or malicious websites.
- Phishing: Phishing is a type of cyber attack that uses email or text messages to trick people into giving up their personal information, such as passwords or credit card numbers.
- DDoS attacks: DDoS attacks are a type of cyber attack that uses multiple computers to flood a target website or server with traffic, causing it to become unavailable.
- Ransomware: Ransomware is a type of cyber attack that encrypts a victim's files and demands a ransom payment in exchange for decrypting them.
Cyber attacks can pose a serious threat to businesses and organizations. They can cause financial damage, disrupt operations, and damage reputation. In order to protect themselves, organizations need to implement a comprehensive cybersecurity strategy that includes:
- Educating employees about cyber security risks
- Implementing strong security measures, such as firewalls and intrusion detection systems
- Backing up data regularly
- Having a disaster recovery plan in place
By implementing these measures, organizations can reduce the risk of a cyber attack and protect themselves from the potential damage that it can cause.



