Endpoint Detection And Response (EDR): Comprehensive Guide To Security Posture Improvement. Endpoint Detection and Response (EDR) solutions have become essential for organizations looking to improve their security posture and protect against advanced threats. but how do you choose the right EDR solution for your organization?
Editor's Notes: "Endpoint Detection And Response (EDR): Comprehensive Guide To Security Posture Improvement" have published today (September 26, 2022). Top cybersecurity concerns that EDR can identify and prevent: unpatched software, phishing and other social engineering attacks, zero-day malware and exploits, insider threats.
To help answer this question, we've analyzed dozens of EDR solutions and interviewed leading security experts. We've put together this comprehensive guide to EDR to help you understand the key features and benefits of EDR, and how to choose the right solution for your organization.
| Key Differences | EDR Solutions | Traditional Antivirus Solutions |
|---|---|---|
| Detection Capabilities | EDR solutions use a variety of techniques to detect threats, including signature-based detection, anomaly detection, and behavioral analysis. | Traditional antivirus solutions rely primarily on signature-based detection, which can only detect known threats. |
| Response Capabilities | EDR solutions provide a variety of response options, including automated remediation, containment, and isolation. | Traditional antivirus solutions typically only offer limited response options, such as quarantining infected files. |
| Visibility and Control | EDR solutions provide comprehensive visibility into endpoint activity, and allow administrators to control and manage endpoints remotely. | Traditional antivirus solutions typically offer limited visibility and control over endpoints. |
EDR solutions offer a number of benefits over traditional antivirus solutions, including:
FAQ
This Frequently Asked Questions section aims to provide clarification and understanding of Endpoint Detection and Response (EDR), a critical security solution for enhancing security posture.

Unveiling the Power of EDR: Enhancing Endpoint Security with Endpoint - Source securitdata.ca
Question 1: What key benefits come with implementing an EDR solution?
EDR solutions empower organizations to swiftly detect and respond to advanced cyber threats, including malware, ransomware, and phishing attacks. They offer real-time visibility and threat intelligence, enabling organizations to proactively identify and mitigate potential breaches.
Question 2: How does EDR assist in threat hunting and incident response?
EDR solutions provide advanced threat hunting capabilities, allowing organizations to actively search for suspicious activities or patterns within their network. They also facilitate rapid incident response, enabling organizations to quickly contain and remediate threats.
Question 3: What are the core components of an effective EDR solution?
Effective EDR solutions typically comprise endpoint agents for real-time data collection and analysis, a management console for centralized control and reporting, threat intelligence to provide context-rich insights, and advanced threat detection algorithms to identify and prioritize security events.
Question 4: How can EDR solutions enhance security posture?
EDR solutions play a crucial role in strengthening security posture by providing enhanced threat visibility, proactive threat detection, automated response capabilities, and continuous monitoring. They offer a comprehensive approach to endpoint security, significantly reducing the risk of successful cyber attacks.
Question 5: What industries and use cases particularly benefit from EDR implementation?
EDR solutions are highly valuable for industries and organizations facing sophisticated cyber threats, such as finance, healthcare, government, and critical infrastructure. They are particularly useful in protecting sensitive data, ensuring regulatory compliance, and maintaining business continuity.
Question 6: How does EDR complement other cybersecurity measures?
EDR solutions seamlessly integrate with existing cybersecurity measures, including firewalls, intrusion detection systems, and antivirus software. By providing an additional layer of defense, EDR enhances the overall security posture and strengthens the organization's ability to defend against a wide range of cyber threats.
In summary, EDR solutions are essential for enhancing security posture and mitigating cyber threats. They empower organizations with advanced threat detection and response capabilities, improving overall cybersecurity effectiveness and reducing the risk of successful attacks.
For further insights into Endpoint Detection and Response, refer to the comprehensive guide.
Tips for Enhanced Security with Endpoint Detection and Response (EDR)
EDR is a powerful tool to strengthen your security posture. Here are some practical tips to maximize its effectiveness:
Tip 1: Continuous Monitoring and Analysis
Deploy EDR solutions that monitor endpoints
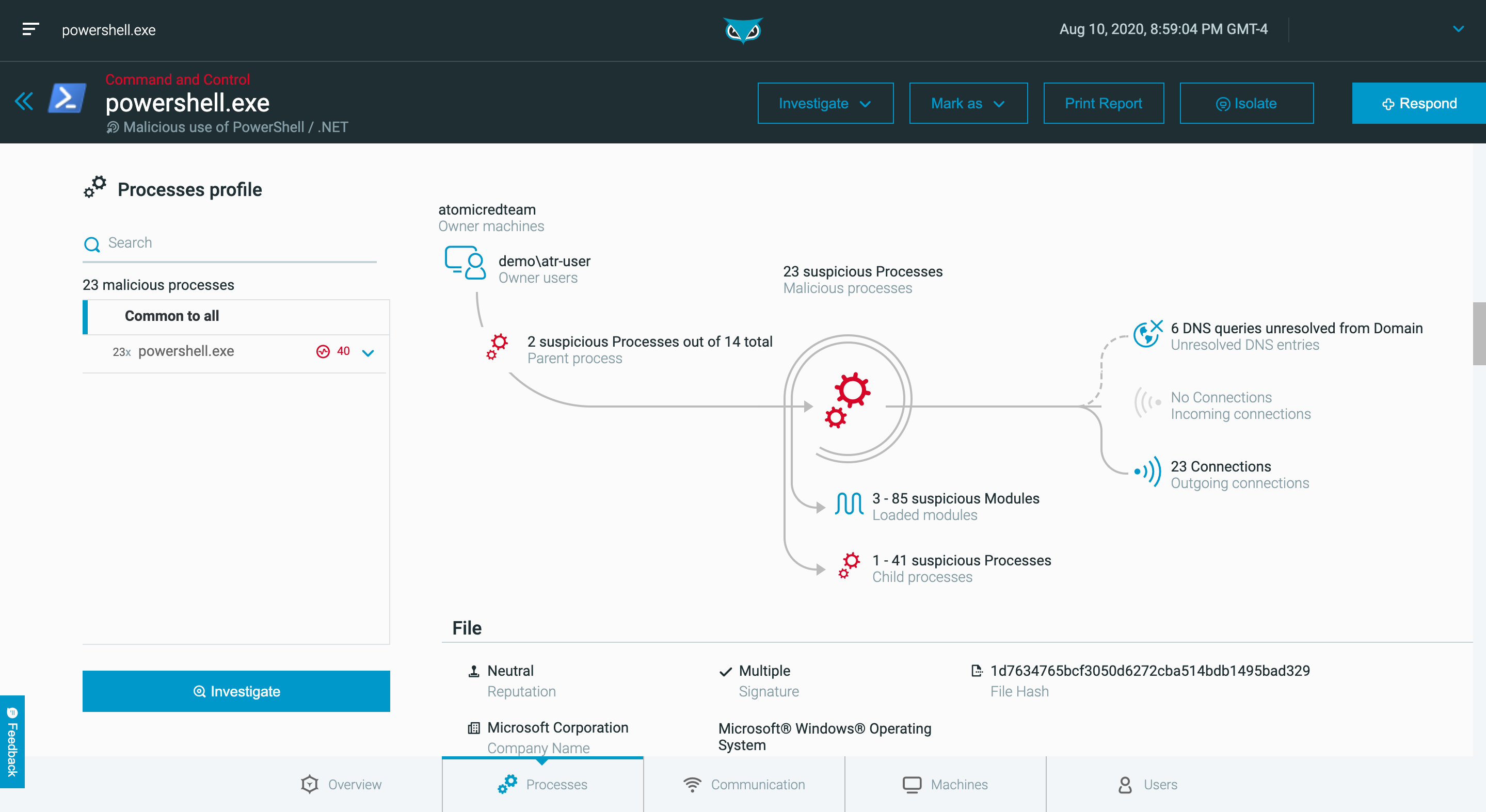
Endpoint Detection and Response (EDR) | Endpoint Security Solution - Source www.cybereason.com
continuously, collecting and analyzing data. This provides a comprehensive view of endpoint activities, enabling rapid detection of suspicious behavior and potential threats.
Tip 2: Threat Intelligence Integration
Integrate EDR with threat intelligence feeds to stay up-to-date with the latest cyber threats. This enables EDR to correlate endpoint data with known attack patterns, allowing it to identify and respond to emerging threats more effectively.
Tip 3: Automated Response and Remediation
Configure EDR to automate response and remediation actions based on pre-defined rules. This automates threat containment, reducing the time window for attackers to exploit vulnerabilities and minimizing the impact of breaches.
Tip 4: Incident Management and Forensics
EDR provides incident management capabilities that streamline investigation and response processes. It also collects forensic data that can be used for post-incident analysis, helping identify the root cause and preventing similar incidents in the future.
Tip 5: Integration with Other Security Tools
Integrate EDR with other security tools such as firewalls, intrusion detection systems, and security information and event management (SIEM) systems. This enables comprehensive threat visibility, enhanced incident response, and improved overall security posture.
By implementing these tips, you can harness the full potential of EDR to achieve a proactive and robust security posture. For a comprehensive guide to security posture improvement with EDR, refer to the Endpoint Detection And Response (EDR): Comprehensive Guide To Security Posture Improvement.
Endpoint Detection And Response (EDR): Comprehensive Guide To Security Posture Improvement
Endpoint Detection and Response (EDR) plays a pivotal role in enhancing an organization's security posture by providing real-time threat detection, investigation, and response capabilities. This comprehensive guide delves into the essential aspects of EDR, empowering security professionals with the knowledge to effectively deploy and utilize this technology.
Effective implementation of EDR requires a holistic approach. By integrating EDR with other security tools, organizations can create a layered defense system that strengthens their overall security posture. EDR plays a crucial role in detecting and responding to threats that evade traditional antivirus and firewall solutions, enabling businesses to stay vigilant against the evolving threat landscape.
Endpoint Detection & Response (EDR) for Comprehensive Cybersecurity - Source wrixte.co
Endpoint Detection And Response (EDR): Comprehensive Guide To Security Posture Improvement
Endpoint Detection and Response (EDR) holds a crucial role in the security landscape, enabling organizations to enhance their security posture by detecting, investigating, and responding to endpoint-based threats. It acts as a defensive shield against malicious activities, providing real-time monitoring, threat analysis, and incident response capabilities.
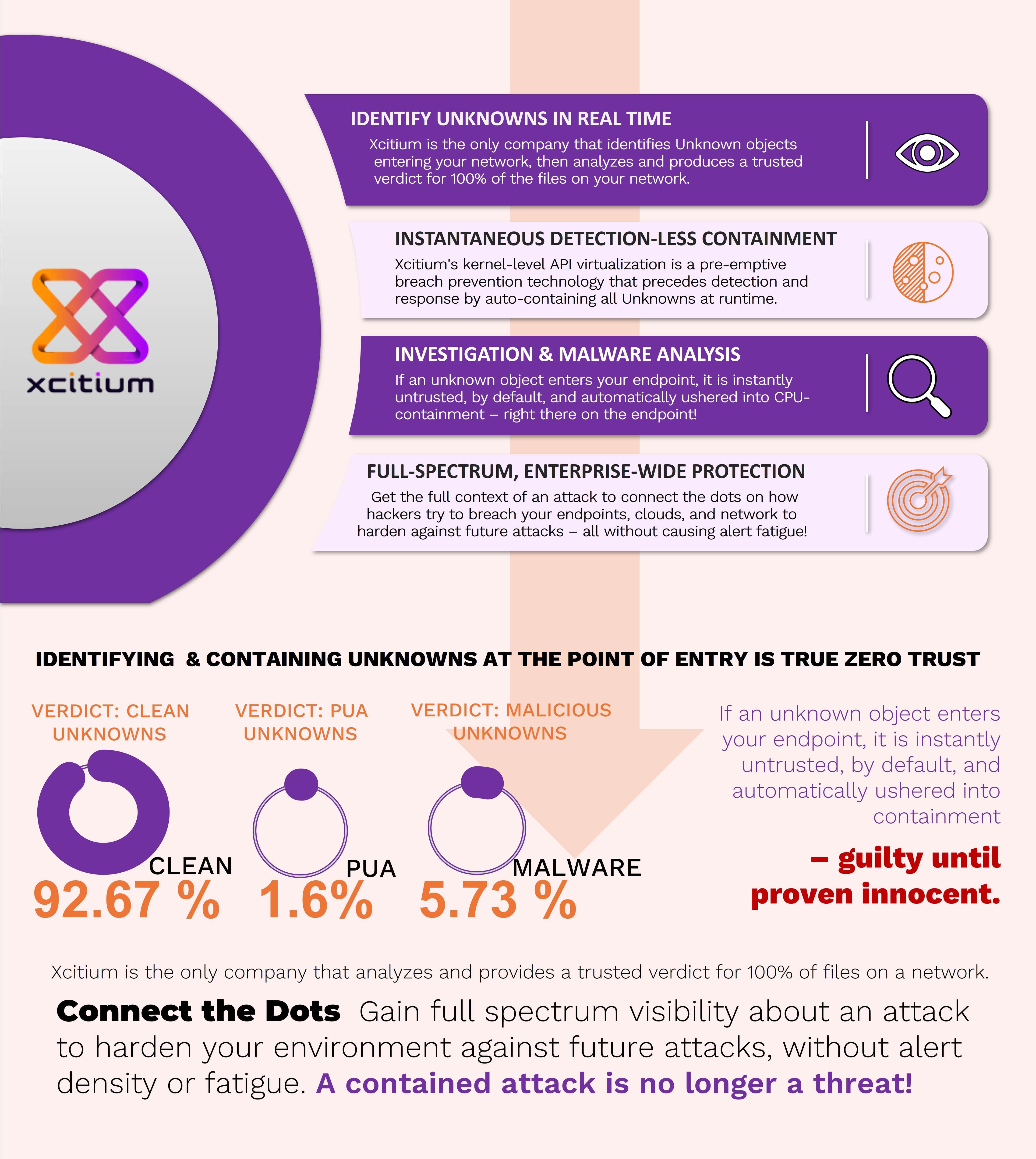
What is EDR? | Definition of Endpoint Detection & Response - Source www.xcitium.com
EDR solutions continuously monitor endpoints for suspicious behavior, collecting and analyzing data from various sources, including system logs, network traffic, and file activity. Upon detecting anomalies, EDR systems generate alerts, enabling security teams to swiftly investigate potential threats. Through advanced analytics and machine learning models, EDR can differentiate between legitimate and malicious activities, reducing false positives and expediting threat response.
The significance of EDR lies in its ability to provide proactive and comprehensive security. By detecting and responding to threats at the endpoint level, EDR prevents adversaries from gaining a foothold within networks. EDR solutions offer a multi-layered defense, enhancing the overall security posture and safeguarding organizations against a wide range of cyber threats.
EDR is an indispensable component of a robust cybersecurity strategy, providing organizations with the tools and capabilities to detect, investigate, and respond to endpoint-based threats effectively. It enables security teams to identify and mitigate risks proactively, reducing the likelihood of successful attacks and minimizing their impact.
| Feature | Description |
|---|---|
| Real-Time Monitoring | Continuous monitoring of endpoints for suspicious behavior |
| Threat Analysis | Advanced analytics and machine learning to differentiate malicious activities |
| Incident Response | Capabilities to investigate and remediate threats swiftly |
Conclusion
Endpoint Detection and Response (EDR) has become an indispensable tool for organizations seeking to improve their security posture. Its real-time monitoring, threat analysis, and incident response capabilities provide a comprehensive defense against endpoint-based threats. By detecting and mitigating risks proactively, EDR enables organizations to reduce the likelihood and impact of successful cyberattacks.
The future of EDR lies in further integration with other security technologies and the adoption of advanced artificial intelligence (AI) techniques. Organizations should embrace EDR solutions as a critical component of their cybersecurity strategy, ensuring they have the necessary tools and expertise to protect against evolving threats and maintain a strong security posture.



